
- A dangerous malware is causing havoc among Mac and Windows users, threatening cryptocurrency wallets.
- The Realst malware employs sophisticated techniques like “AppleScript spoofing,” password division, and keychain data extraction.
- Stay vigilant and learn how to spot threats to your wallets.
Introduction
Hackers remain undeterred as governments turn a firm eye to the prevalence of cybercrime in the crypto space. Ever seeking innovations in exploitation, July has been an active period for hackers as a Coinbase user lost $4.2M to an attack known as “spear phishing.
On July 6th, security researcher iamdeadlyz identified a new threat to users’ crypto wallets, known as “Realst,” and dragged it into the spotlight.
16 Distinct Variants Pose Cryptocurrency Threat
The Realst malware affects users on both Windows and Mac by spreading through fake blockchain games. Threat actors use social media to promote games and share access codes for downloading. Access codes are then used to target victims’ wallets and evade security researchers.
Sponsored
Game installers distribute data-stealing malware (e.g., RedLine Stealer on Windows, Realst on macOS), which pilfers data from web browsers and cryptocurrency wallets. SentinelOne analyzed 59 Mach-O samples of Realst, discovering 16 variants, highlighting active development.
As per SentinelOne’s analysis, the Realst malware has these variants categorized into families A, B, C, and D.
| Family | Description |
| Family A | Uses “AppleScript spoofing” to trick victims into typing admin passwords. |
| Family B | Divides strings for password spoofing, evading static detection. |
| Family C | Contains “chainbreaker” reference, extracting data from the system’s keychain. |
| Family D | Prompts victims in Terminal, dumping saved credentials from Keychain. |
Each family employs different techniques to gain unauthorized access to user information, exploiting vulnerabilities in browsers and cryptocurrency wallet apps. The malware has targeted macOS 14 Sonoma, indicating the ongoing and rapid development of the threat.
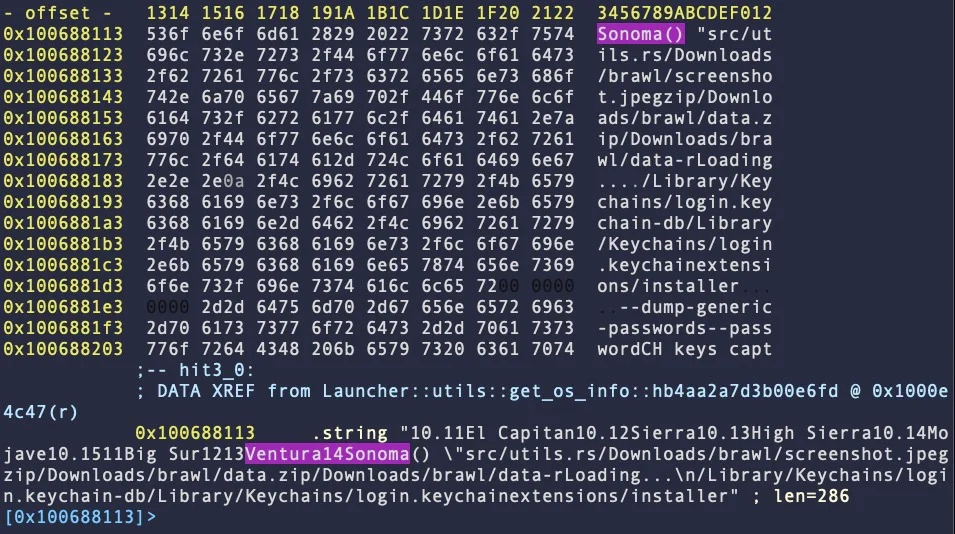
To defend yourself from this multifaceted danger, it is crucial to understand how the malware spreads and the potential risks it poses to your crypto assets.
Defend Yourself from Realst Malware
Realst malware spreads by luring Windows and macOS users into downloading fake blockchain games like Brawl Earth, WildWorld, Dawnland, Destruction, Evolion, Pearl, Olymp of Reptiles, and SaintLegend. When downloading these games, the Realst info-stealing malware comes as part of the package in the form of PKG or DMG files.
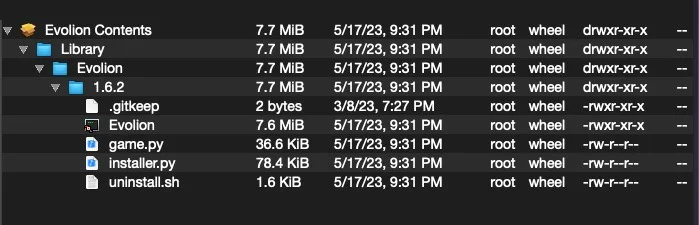
The malware utilizes “game.py” and “installer.py” files to steal data, compromising web browsers and cryptocurrency wallets.
It is uncertain whether deleting these files would adequately mitigate the threat. As such, due diligence and research into new blockchain games before downloading remain the best prevention methods.
On the Flipside
- SentinelOne discovered that certain samples are codesigned using valid (now revoked) Apple Developer IDs or ad-hoc signatures, enabling them to evade detection by security tools.
- The malware’s active development and preparation for macOS 14 Sonoma indicate potential future attacks.
Why This Matters
According to security researcher iamdeadlyz, the malware is part of a massive campaign targeting Windows and macOS users. Its ability to steal data from cryptocurrency wallets and web browsers poses a severe risk to users’ financial security and privacy.
To learn more about crypto’s most wanted criminals: Ruja Ignatova and other cryptocurrency crooks, click here:
Crypto’s Most Wanted Criminals: Ruja Ignatova and Other Cryptocurrency Crooks
To know more about Island Pay teaming up with Circle’s USDC for swift and low-cost crypto remittances, click here:
Island Pay Teams Up with Circle’s USDC for Swift and Low-Cost Crypto Remittances
