Since the coronavirus became a global pandemic and the hottest topic around the news, cybercriminals are also on track and using it for their profit.
The sudden spike of over 2 500 infections from two malware strains spread by coronavirus-themed emails was discovered this Monday by Jiri Kopac, a researcher at cybersecurity company ESET. The Forbes reports, that the number of malicious attacks might be the biggest COVID-19-related malware campaign ever seen, especially to compare with dozens of attacks just a few days before.
Malicious emails
According to the cybersecurity researcher, the most-targeted countries were Spain, Portugal, Czech Republic, Malaysia, and Germany. Hackers only targeted Microsoft Windows devices.
The specialist said, the malware mainly operated in two separate ways: by trying to affect a computer in order to download more malicious software or stealing personal data from an infected device.
The malicious scam came as phishing emails promising information on vaccines or ways how to protect yourself from coronavirus if the reader clicks on an infected attachment.
Proofpoint cybersecurity company also monitored a massive surge in the coronavirus-related attacks this week. The company observed credential phishing, malicious attachments, malicious links, business email compromise (BEC), fake landing pages, downloaders, spam, and malware, among others, all leveraging coronavirus lures. According to their report on March 16th, the main targets are based in the United States:
Over the past week, the team observed a campaign from TA505, the group behind Locky ransomware and the Dridex banking Trojan, that uses a coronavirus lure as part of a downloader campaign targeting the U.S. healthcare, manufacturing, and pharmaceuticals industries.
TA505 is known as one of the most significant financially motivated threat actors due to the extraordinary volumes of messages they send. This is how their malicious email, that urges to click on a provided link, looks like:
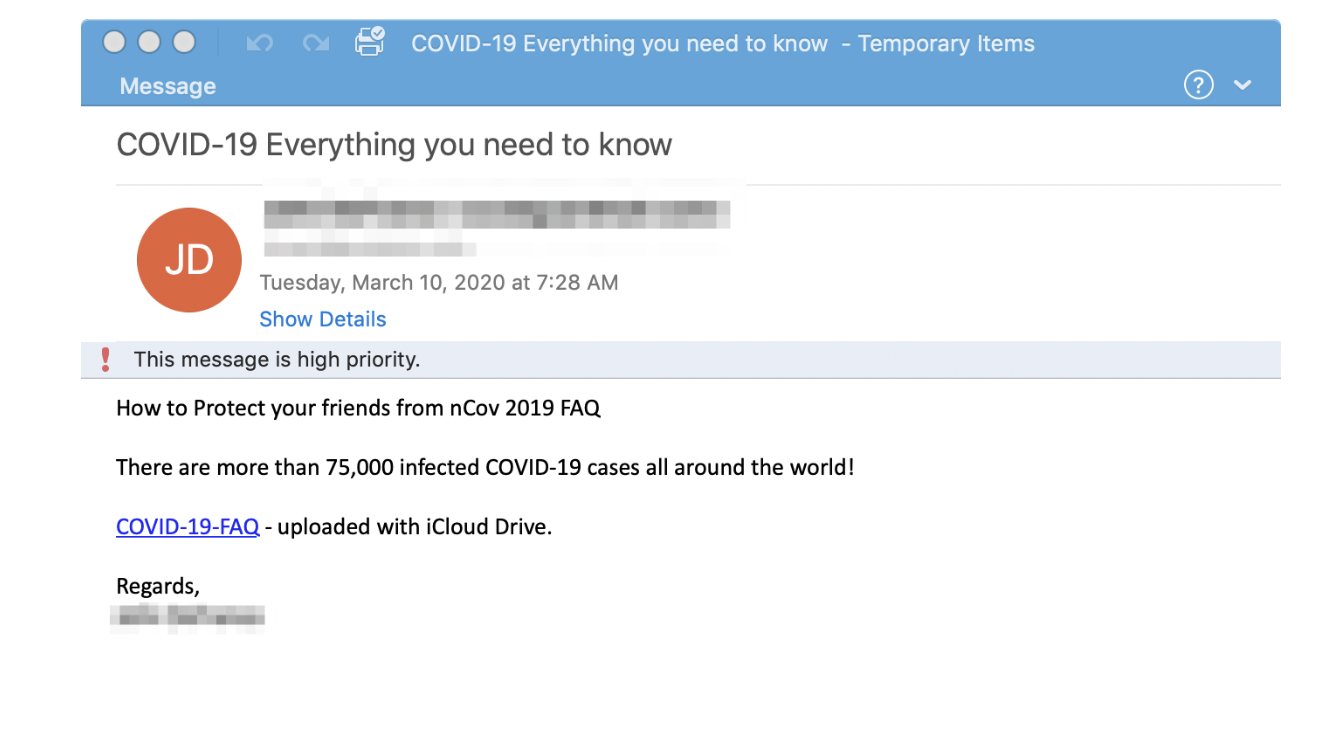
The Proofpoint says its team has additionally seen TA564 using coronavirus emails to target Canadian users by spoofing the Public Health Agency of Canada in an attempt to deliver Ursnif.
Risky websites
In prior weeks cybercriminals have registered a vast number of potentially-malicious websites, that use domain names related to coronavirus or COVID-19.
The National Cyber Security Centre of the United Kingdom reported an increase in the registration of webpages relating to the Coronavirus suggesting that cybercriminals are likely to be taking advantage of the outbreak.
The cybersecurity officers recently have revealed a range of attacks being perpetrated online. According to them, the attacks are versatile and can be conducted through various media, adapted to different sectors and monetized via multiple means, including ransomware, credential theft, bitcoin or fraud.
Fraudulent maps
Another big threat is malicious coronavirus maps circulating on the internet, that secretly plants malware to steal information from the victim’s computer.
Hackers do target people by using one of the most reliable online tools for information about coronavirus pandemic, a legitimate COVID-19 threat map created by Johns Hopkins University’s Center for Systems Science and Engineering.
Mimicking its authentic dashboard, the fake map of the globe highlights to locations of confirmed and suspected COVID-19 cases, together with the statistics of the deaths and recoveries related to the coronavirus.
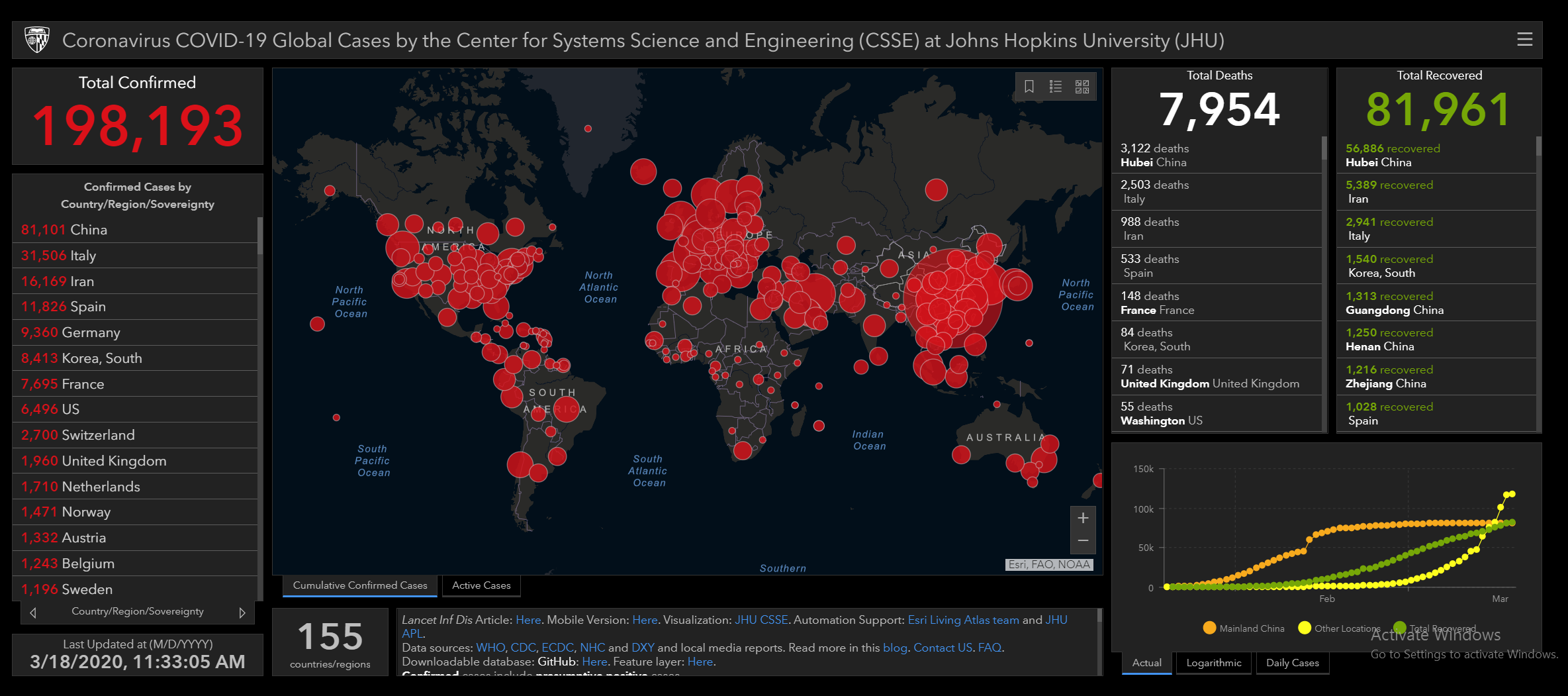
The credentials such as user names, passwords, credit card numbers, and other sensitive information are the main targets here.
Ransomware app
Since cybercriminals use all their wide arsenal to bait the victims, the mobile devices are not the exception.
The cyber threat intelligence company DomainTools reported, that their cybersecurity research team recently discovered the suspicious domain (coronavirusapp[.]site) that claims to have a real-time COVID-19 outbreak tracker available to download via the Android application.
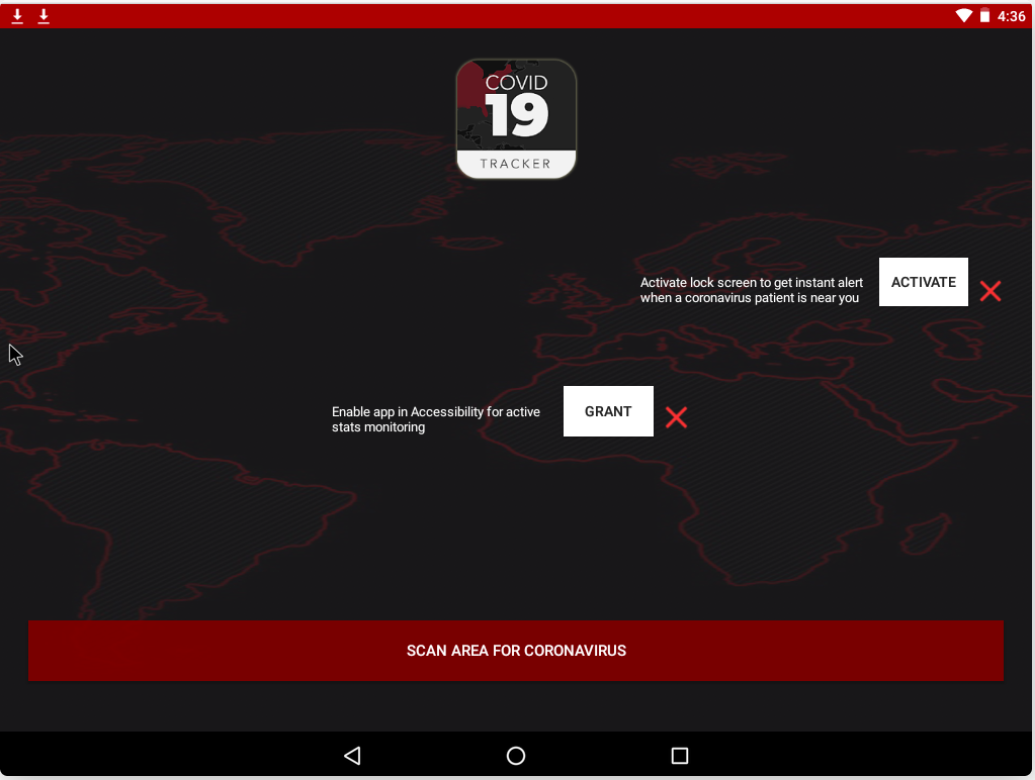
The fraudulent app pretends to give access to a coronavirus map tracker to provide current statistical information about the COVID-19 cases in the user’s nearest environment. Meanwhile, the malicious software locks the screen of the mobile device and demands $100 in Bitcoins for the unlocking.
The app even threatens to erase contacts, pictures, and videos, as well as the phone’s memory. It even claims to leak social media accounts publicly.

Despite the strict quarantine measures in dozens of countries, the COVID-19 outbreak continues to spread. As the numbers of infected persons are still increasing, experts forecast that life around the world might be disrupted for many months.
