
Numerous Ukrainian government websites went down due to the massive cyberattack earlier this month.
Destructive malware targeted the websites of Ukraine’s ministry of foreign affairs, security and defense council, ministry of education, several other governmental agencies, and a related IT firm while the country faces the biggest threat yet of Russian military invasion and stands at the edge of war.
The series of cyber attacks started with a $10,000 ransom demand in Bitcoin, which later became irrelevant for the hackers.
Sponsored
Ukrainian authorities are running an investigation, although perpetrators have not been identified yet. The country has experienced numerous cyberwar assaults originating from Russia in the past.
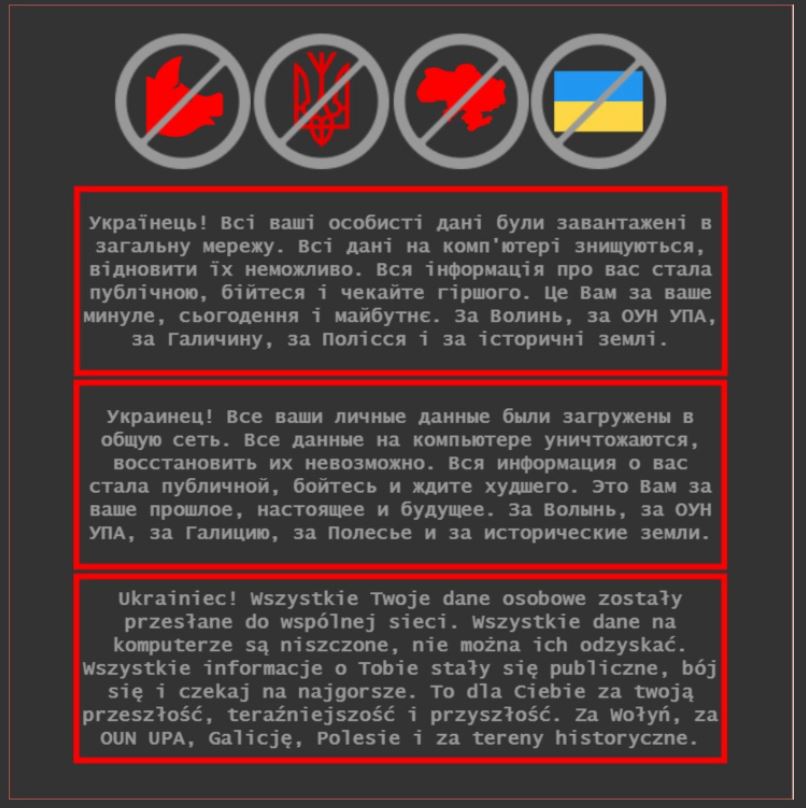
“This is because of your past, present and future”
The attacks hit the Ukrainian state websites with dramatic messages on their title pages stating that all their data was leaked and wiped out from computers due to political reasons.
“Ukrainian! All your data were uploaded into a public network. All data on computer is deleted without a possibility to restore. All information about you became public; be afraid and hope for the worse. This is because of your past, present, and future. Because of Volyn [Ukrainian city - DailyCoin], OUN UPA [Ukrainian Rebel Army - DailyCoin], Galicia, Polissya, and historical lands.” - declared the anonymous hackers.
The statement addressed each and every Ukrainian and came in three languages including Polish and Russian. It also depicted a crossed-out Ukrainian flag, coat of arms, a silhouette of Ukrainian territory, and a pig’s head above the text.
However, the senior official of Ukraine’s cybersecurity agency, Viktor Zora, revealed the first attacks started a day before such a message was shared on government websites.
Sponsored
According to him, the website admins first faced a $10,000 in Bitcoin ransom demand for accessing their data. Yet the administrators found irreparably damaged computer hard drives after rebooting.
A Complex Attack
As later stated by the Ukrainian cyber police, a number of external information resources were manually destroyed by hackers during a coordinated and complex attack.
Ukrainian cyber police revealed that the perpetrators used three attack vectors, including supply chain attack, exploitation of content management system OctoberCMS and vulnerabilities of Log4j, a Java-based logging utility. A day before that, affected institutions were hit by DDOS attacks.
Investigators claimed that “short deadlines for the attack indicate the coordination of hackers’ actions and their number”.
Although the absolute majority of the hacked government websites have resumed their work in a few days, the initiators of the fake Bitcoin ransom message and data-wiping attacks have not been identified.
Sandworm Again?
The recent attacks on Ukrainian state institutions, however, have similarities with the cyberwar actions taken against Ukraine right before Christmas in 2015.
The country’s government agencies, treasury, railway system, media companies, and even national power grid were hit by malware attacks. The attack over the power grid led to outages for nearly a quarter of a million citizens and was one of the first publicly known successful cyberattacks on such an object.
The acts of cyberwar in 2015 happened during the Russian military intervention into Ukraine’s territory. They were also related to Sandworm, a Russian cyberwar unit of the GRU, the organization in charge of Russian military intelligence.
A New Dimension of Ransomware Threat
The cyberattacks on the Ukrainian institutions raised some eyebrows among the cybersecurity community. Although attackers imitated the ransom intentions, their real target was data and data destruction, experts say.
“The malware is designed to look like ransomware but lacks a ransom recovery mechanism. This means that the malware “is designed to render targeted devices inoperable rather than to obtain a ransom” the Microsoft Threat Intelligence Centre writes in its blog post.
According to cybersecurity experts, such usage of malware might “mark the beginning of a new dimension of the ransomware threat”.
Fewer and fewer companies worldwide agree to pay ransoms to redeem stolen data. This leads cybercriminal groups into finding new tactics like in-advance data destruction for those who refuse to pay and cooperate.
Why You Should Care
Ukraine, the second-largest country by area in Europe, is at the edge of war with the Russian Federation, which mobilized a massive 100,000 troops and missiles on the Ukrainian border. The Kremlin sees the sovereign country as a part of Russia and is against its strengthening ties with the democratic West. NATO member countries are sending military hardware to support Ukraine in response to the Russian military threat. The military tension in Europe is the biggest since World War II.
